The Launch command
Back in 2008, Adobe decided to allow for opening attachments within their document format PDF using external applications (ISO PDF 32000-1:2008). For example, if you attached a nice Excel spreadsheet to your PDF presentation, Adobe Reader or Acrobat would use Microsoft Word, Star Office, or Open Office to open the Excel document. Adobe added this “feature” called Launch to the PDF specifications for enhancement reasons, but the entire effort was short sighted from the get-go.
Although, it sounds nice to have the ability to use other applications to open attachments, it also opens the PDF specification to abuse from those “evil” hackers out there. We have been bombarded constantly since last year with Adobe issues from Acrobat/Reader to Flash. This is only the newest issue in a long line of hardships for (poor?) Adobe. Launch can be used to execute commands from the PDF document, normally to open Word or whatever to view the attachment. Although designed for benign use, this can also be used to execute just about anything on your machine. Because the PDF specification is platform independent meaning there are PDF readers for Windows, Mac, and Linux platforms, all of them conform to the same specifications laid out by Adobe. So, all of these OSs are prone to the attack using this vulnerability in the PDF spec.
A sample, but real attack and how to disable Launch
The attack goes a little like this: Someone sends you a PDF attachment in an email. This email could be a targeted-spearphishing attack which specifically targets your company or organization with a subject line that goes something like “Your account has been disabled”. The PDF looks harmless enough from the outside, possibly giving instructions to perform some actions on your computer or simply “Open the Attachment” or in very large text. What is happening under the hood though is very worrisome as it builds on previous attack vectors using Adobe products and using the Launch command which…
- Reads the PDF document for commented out code. Comments in PDF’s are signified by a % character. To execute this command, the PDF Launch command will execute everything at first using cmd.exe. So, this particular attack is Windows-based, but remember — this could easily be /bin/cat as well; affecting many other OSs.
- All of the comments are written to a file named script.vbs. The comments are doubly commented, so the Launch command, actually using cmd.exe to do this, also reads the comments (again) removing the comments characters and writing a file named batscript.vbs.
- The final step for the PDF to do is execute the script.vbs and batscript.vbs files it just wrote.
So, what do these VBScripts do? They write a new file named game.exe which is actually virus, but it could be anything really at the end of the day. The point here to take away from all of this is to not trust Adobe’s Launch feature at all. Users should disable the automatic launch of external applications to open attachments by…
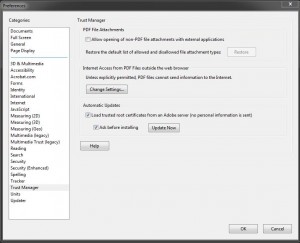
- In Adobe Reader and Acrobat, click Edit menu then click Preferences.
- In the Trust Manager Category, uncheck Allow opening of non-PDF file attachment with external applications box.
Adobe fail part deux
Another issue here is how Adobe short-sighted the design of Reader/Acrobat so that attackers could use this attack more efficiently. When a PDF has a Launch command within it, Reader/Acrobat will ask you whether or not you would like to execute the command(s). Adobe will list the command verbatim within a multi-lined textbox which is not disabled, but looks like it should be as it is grayed-out. Unfortunately, since Adobe lists the command(s) verbatim, an attacker can insert whitespaces and/or carriage-returns which, in combination with the appearance of a grayed-out textbox, hides the commands from the user. Because this is a targeted-spearphishing attack, the user will likely open the document, see the obfuscated commands as “Click the open button to continue…” or something and click to execute the commands unknowingly infecting themselves with a virus. This is a real design flaw by Adobe which only exacerbates the overall security issues already present in their products.
If you disable the automatic opening of attachments with external applications, as shown above, you will instead be prompted with a simple dialog which states that these commands were designed to be executed but didn’t. This should protect you from the attack vectors laid out above. You can always detach PDF attachments and open them separately using the applications themselves (i.e. Word) without using the built-in Adobe Launch command.
For more information, see Adobe’s response to this attack: Didier Stevens on the Launch Function.